What Is Spoofing, and How Can You Spot It?
Updated: Jan. 12, 2023

Spoofing is a funny word, but its consequences are serious. Here's how spoofing works, the many forms it can take and how to protect yourself against it.
Just when you think you know how to avoid security threats online, cybercriminals keep getting savvier. Spoofing—a scam in which a criminal pretends to be someone else so they can commit fraud, spread malware or carry out other cyberattacks—is the latest in a long list of online scams to keep on your radar.
Here’s the good news: Taking simple security measures, like learning about spam texts to delete immediately, the area codes phone scam and the four-word phone scam, can make it harder for fraudsters to fool you. To help you stay safe, we’ve asked cybersecurity experts to explain how spoofing works and what you can do to avoid falling victim to online scams.
What is an example of spoofing?
A spoofing scam might be an email, text message or phone call that appears to be from a trusted source, like a loved one or even a popular brand. But in reality, a fraudster is behind the fake email address or phone number, hoping to convince you to download malicious software, send money or share personal information or data with them.
Spoofing attacks can take many forms. In one recent example, hackers created phony Zoom invitations for virtual meetings at community associations and school boards. Victims who clicked on the document attached to the emails infected their devices with malware. Other examples of spoofing include emails posing as a request from PayPal or eBay for your login information, or text messages that appear to be money transfers from an online wallet or bank.
Is spoofing a crime?
Spoofed emails, phone calls or text messages that lead to criminal acts such as attempted hacking, fraud or financial theft are illegal, according to Karim Hijazi, CEO of cyber intelligence company Prevailion and a former contractor for the U.S. intelligence community. It happens more often than you think too. In a recent FBI report, people reported losing more than $82 million to spoofing scams in 2021.
If you are the victim of spoofing or other online fraud, you can file a complaint with the FBI’s Internet Crime Complaint Center (IC3), as well as your local police station if you lost money. FYI, these Venmo scams, Amazon scams and Facebook Marketplace scams could also steal your money.
Spoofing by text
How it works
In spoofed text messages, fraudsters disguise their sender ID to appear as someone or something they are not. They might claim to be your boss or family member, or they might impersonate a familiar company like Amazon or your bank. Either way, their goal is to trick you into sharing personal data or clicking a link that infects your phone with a virus.
Unfortunately, it’s now easier than ever to create spoofed text messages. Most criminals use a software that allows them to create any sender ID they choose. “It used to require a business phone system to spoof caller ID, but now anyone can download an app from the App Store enabling them to make spoofed calls or texts,” says Aaron Higbee, co-founder and chief technology officer at cybersecurity firm Cofense.
Why it’s dangerous
The biggest danger of spoofing by text message: It is extremely difficult and sometimes impossible to recognize. “Spoofed text messages can sometimes be indistinguishable from legitimate messages, so the reader really has to pay attention,” says Andrew Barratt, vice president of technology and enterprise at cybersecurity firm Coalfire.
Not only are spoofing texts tough to spot, but they can also cause serious harm to victims. For example, by clicking a link attached to the text message, you could accidentally download malware that allows someone to spy on your iPhone. If a fraudster can convince you that they are from your bank, you might share financial or other sensitive information with them. Victims can also be fooled into sending money to a criminal if they believe they are texting a loved one.
How to recognize a spoofing text
Beware of any text message from a phone number that you don’t recognize, says Higbee. If you receive a message that appears to be a fraud detection or billing alert from a company you do business with, like your bank, look up the company’s publicly listed number and call them directly to confirm the message. These alerts are among the most popular tricks that fraudsters use today, Higbee says. You should also learn how to stop spam texts in the first place.
Spoofing by phone call
How it works
Like spoofed text messages, spoofing by phone call relies on technology that allows criminals to create a fake caller ID. Then they can place calls pretending to be Amazon, PayPal, your bank or any other familiar business in order to steal money or sensitive information.
For example, attackers may call someone to warn them about a fraud alert on their account and then offer to help, according to Higbee. By tricking the victim into sharing their login information, fraudsters can gain access to the person’s account and to any sensitive data it contains, like credit card numbers. These free password managers can help keep your log-ins secure from hackers.
Why it’s dangerous
People often fall victim to spoofed phone calls because mobile carriers are not able to block these calls or alert people that the call may be a scam, according to Hijazi. “For the recipient of the call, everything appears legitimate,” he says. “When your bank’s name appears in your caller ID, it’s easy to be fooled.”
Hijazi also notes that criminal call centers have gotten very good at imitating the real customer service procedures of legitimate organizations like banks, which makes it even harder for the victim to realize they’re being conned. Stay ahead of spoofing phone calls by learning how to stop robocalls for good.
How to recognize a spoofing call
If you receive a suspicious call, Barratt recommends paying attention to the quality of the audio. “The perpetrator is likely to be using a low-grade internet phone service that results in poor call quality,” he says. Always verify that the call is legitimate by contacting the company directly before handing over any sensitive information like your login credentials or credit card numbers.
Urgent requests to share information, send money, click a link or download an attachment should be viewed with suspicion, according to Hijazi. “These scammers are very good at preying on our anxieties, and they will also try to move quickly to prevent the person from having time to think,” he says.
Spoofing by email
How it works
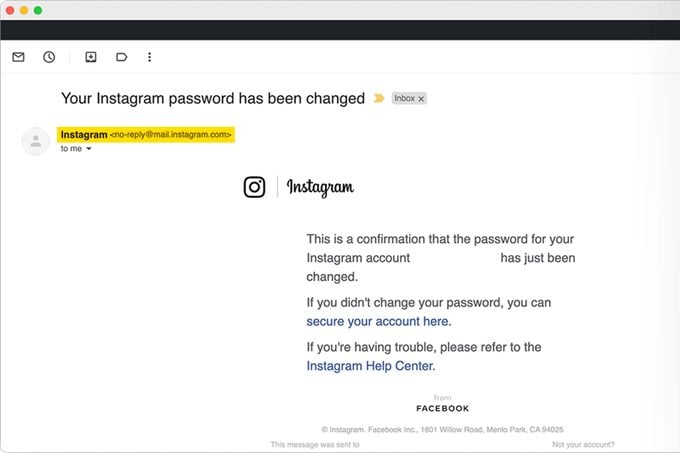
Believe it or not, spoofing is one of the many things hackers can do with just your email address. “Email historically has been very [easy] to spoof,” Barratt says. All fraudsters need to do is create a forged sender address that looks like yours, making small and tough-to-spot changes, like adding a period or swapping a number with a letter. Then they use the email address to send “spoof” messages containing harmful malware or urgent requests for money.
Keep in mind that “spoofing isn’t the same thing as hacking,” Hijazi says. “When a person’s email is spoofed, it hasn’t actually been compromised by the hacker. It’s just been copied.”
You could receive spoofed emails too. With email spoofing, attackers are hoping to fool you by assuming the identity of a person or organization you know and asking you for money, sensitive information or other favors. The sender’s title mimics the real person’s or organization’s name, but the email address is slightly different from their actual one.
Why it’s dangerous
A spoofed email address looks legitimate, so email spoofing allows scammers to bypass the spam filters on most email accounts. Once spoofed emails make it into an inbox, victims are much more likely to open and fall for them. “People assume that when a sender’s name appears in their inbox, it’s the real person,” Hijazi says. “But this is very easy to fake.” Email is also one of the most sought after scam methods, such as in the Geek Sqaud scams for instance.
Email spoofing is the number one way people and companies get hacked, according to Hijazi. “You can be scammed out of money or personal information, lose access to your accounts or wind up with a malware infection on your device,” he says. Malware attacks that rely on phishing emails, such as these Apple ID phishing scams, are on the rise as well.
What’s more, spoofed emails might be linked to sextortion schemes, which lure the victim into engaging in a private conversation or sending sensitive images of themselves that are later used for blackmail. Hackers may also impersonate a law enforcement agency and claim they have proof that you have engaged in illegal activities, like accessing child pornography, Hijazi warns.
How to recognize a spoofing email
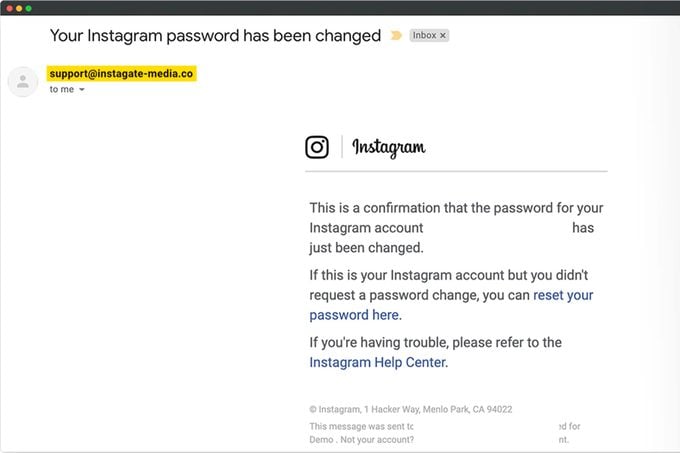
Receiving any emails from a contact through a new sender address should be a red flag that you might be dealing with a spoofing attack. Higbee advises being skeptical of any explanation as to why the sender is using a new email address. “When an attacker spoofs the friendly name, they will usually have a lie to explain why they are using a new email address,” he says. Instead, reach out to your contact in person or by phone call to confirm that the message is real.
For spoofing emails from companies or brands, Hijazi recommends checking the sender address to make sure it matches the sender’s name and actual email address. He also suggests looking for grammar and spelling mistakes, as well as any errors in the email format, which could indicate the email is not legitimate.
Luckily, “many online mail providers are already picking up spoof emails with the additional security they provide to help users with spam,” Barratt says. Still, you should always stay alert for spoofing emails and other phishing attacks in your inbox.
Other types of spoofing
There are many other types of online spoofing to watch out for, and not all of it is related to financial fraud, experts say. For example, name spoofing—when fraudsters spoof the names of people with large audiences online to promote pyramid schemes or cryptocurrencies—is common on Twitter, YouTube and other social media platforms, Higbee says.
Don’t assume screenshots of text messages are legitimate, either, Higbee says. People can fabricate a conversation with someone by spoofing their phone number, screenshotting it and claiming the messages are a real conversation. This can cause personal and reputational damage for the spoofed person.
To keep your own info from falling into the wrong hands—and potentially leading to a spoofing attack—know the security risks of using public Wi-Fi networks and prevent companies from buying and selling your personal information.
Sources:
- Karim Hijazi, CEO of Prevailion
- Aaron Higbee, co-founder and chief technology officer at Cofense
- Andrew Barratt, vice president of technology and enterprise at Coalfire
- FBI: “Internet Crime Report 2021”
- Avanan: “Local Meetings Under Attack”



